I’ve decided to implement monitoring for my homelab through a cloud virtual machine. As cloud provider I’ve opted for Hetzner, but more on that in a future post.
To enhance the security of this setup, I’ve chosen to establish the cloud VM from Hetzner as the single entry point to my infrastructure. For this purpose, I’ve opted to use Tailscale for tunneling, not only for client-to-site but also for site-to-site connectivity.
Tailscale Site-to-Site Networking
Information provided by Tailscale:
Note
Use site-to-site layer 3 (L3) networking to connect two subnets on your Tailscale network with each other. The two subnets are each required to provide a subnet router but their devices do not need to install Tailscale. This scenario applies to Linux subnet routers only.
Warning
This scenario will not work on subnets with overlapping CIDR ranges, nor with 4via6 subnet routing.
Network Architecture
In my case, there are two private subnets without any connectivity between them:
- Subnet 1 - Homelab: 10.57.57.0/24
- Subnet 2 - Cloudlab: 192.168.57.0/24
IP addresses of the routers for each subnet:
- Subnet 1: 10.57.57.1 (pfSense)
- Subnet 2: 192.168.57.254 (Linux VM)
Setting up Tailscale on pfSense (Subnet I)
Let’s dive into the configuration. Due to pfSense being based on FreeBSD and Tailscale not offering as much support for pfSense as for other platforms, this configuration is a bit trickier.
Install Tailscale on pfSense
- Navigate to System > Package Manager in the pfSense web interface
- Click on the Available Packages tab
- Search for
tailscaleand click Install
Configure Tailscale on pfSense
Navigate to VPN > Tailscale
Authentication
- Copy auth-key from https://login.tailscale.com/admin/settings/keys
- Generate Auth keys
Basic Configuration
- ✅ Enable tailscale
- Listen port: leave as default
- ✅ Accept Subnet Routes
- ✅ Advertise Exit Node (optional)
- Advertised Routes: 10.57.57.0/24
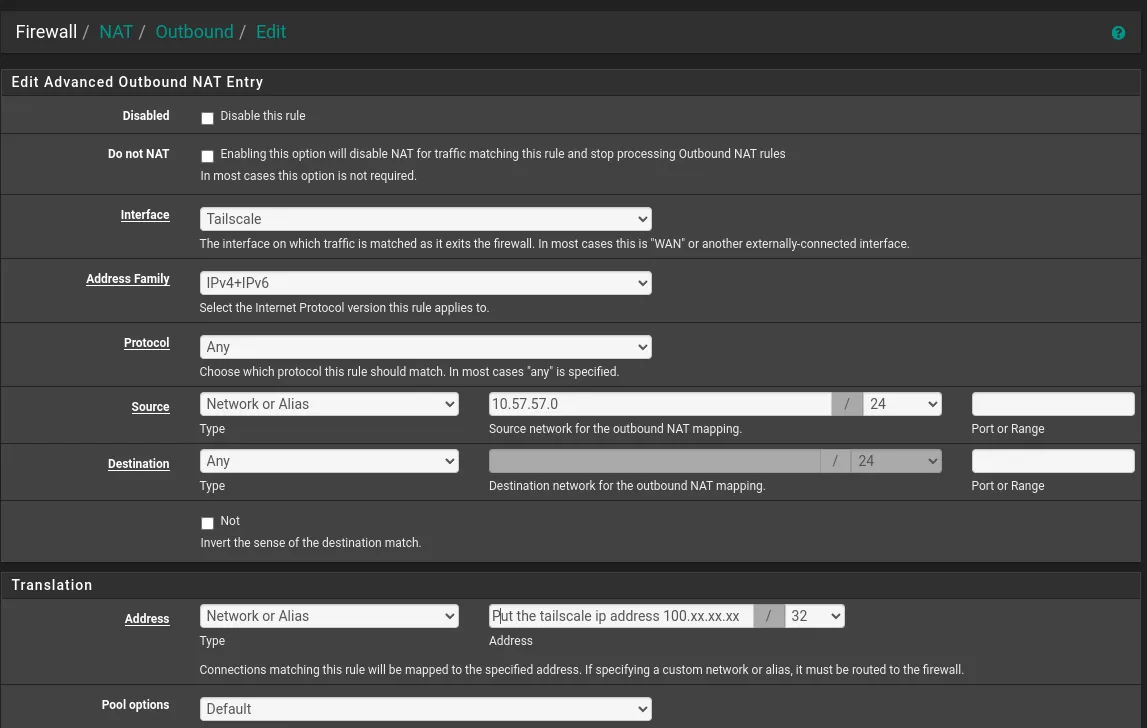
Tricky Part: Outbound NAT Rules
Navigate to Firewall > NAT > Outbound
Configure Outbound NAT Mode
Set to: Hybrid Outbound NAT
Create Manual Mapping
- Interface: Tailscale
- Address Family: IPv4+IPv6
- Protocol: Any
- Source Network or Alias: 10.57.57.0/24
- Destination: Any
Warning
This part is broken from last update [23.09.1] so NAT Alias is missing.
Workaround:
- Translation section:
- Address: Network or Alias
- Put the tailscale IP address:
100.xx.xx.xx/32
This is how it should look:
Configure Tailscale on Linux VM (Subnet II)
Install Tailscale and Enable Routing
# Install tailscalecurl -sSL https://tailscale.com/install.sh | sh
# Activate routing for IPv4echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.conf
# Activate routing for IPv6echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.conf
# Apply routing configuration at kernel levelsudo sysctl -p /etc/sysctl.confAdvertise Routes on Linux
On the 192.168.57.254 device, advertise routes for 192.168.57.0/24:
tailscale up --advertise-routes=192.168.57.0/24 --snat-subnet-routes=false --accept-routesCommand explained:
--advertise-routes: Exposes the physical subnet routes to your entire Tailscale network--snat-subnet-routes=false: Disables source NAT. In normal operations, a subnet device will see the traffic originating from the subnet router. This simplifies routing, but does not allow traversing multiple networks. By disabling source NAT, the end machine sees the LAN IP address of the originating machine as the source--accept-routes: Accepts the advertised route of the other subnet router, as well as any other nodes that are subnet routers
Enable Subnet Routes from Admin Console
Note
This step is not required if using autoApprovers.
- Open the Machines page of the admin console
- Locate the devices configured as subnet routers (look for the Subnets badge or use the
property:subnetfilter) - For each device, click the ellipsis icon menu and select Edit route settings
- In the Edit route settings panel, approve the device
Tip
The Tailscale side of the routing is complete!
Credits
- Tailscale Documentation - Official site-to-site networking guide
- Christian McDonald - Helpful YouTube tutorial on pfSense Tailscale setup