When Oracle Cloud announced their generous Always Free tier with ARM-based Ampere instances offering up to 4 OCPUs and 24GB RAM, it opened up incredible opportunities for homelab enthusiasts. Combined with 200GB of block storage and unlimited ingress traffic, it’s the perfect platform for off-site Synology NAS backups—completely free.
But there’s a catch: Oracle Cloud’s security defaults are aggressive, and getting Synology HyperBackup to work with rsync over SSH requires specific configuration steps that aren’t immediately obvious.
Note
This guide assumes you already have an Oracle Cloud Always Free instance running Ubuntu and Tailscale configured for secure connectivity. If you’re new to Tailscale, check out their homelab documentation first—it’s a game-changer for secure remote access without port forwarding.
Why This Setup?
After exploring various backup solutions, this configuration offers the best balance of security, cost, and reliability:
- Zero cost: Oracle Cloud Always Free tier + Tailscale free tier
- Secure: Encrypted over Tailscale VPN, no public exposure
- Reliable: rsync’s incremental backups minimize transfer time
- Flexible: 200GB block storage with 5 volume backups included
The alternative would be Synology C2 or other cloud backup services, but those cost $60-120/year for similar storage. With Oracle Cloud, it’s completely free forever.
Prerequisites
- Synology NAS with HyperBackup package installed
- Oracle Cloud Always Free account with Ubuntu instance
- Tailscale installed on both NAS and Oracle Cloud instance
- Basic SSH access to your Ubuntu instance
The Oracle Cloud SSH Challenge
Here’s where most guides fail: Oracle Cloud disables password authentication by default in /etc/ssh/sshd_config, but HyperBackup needs it to establish initial connections before you can set up SSH keys.
When I first tried connecting, I hit this error:
ash-4.4# ssh synology-backup@100.100.100.100synology-backup@100.72.22.38: Permission denied (publickey).The issue? Oracle Cloud’s SSH configuration explicitly blocks password authentication, even if you think you’ve enabled it.
Setting Up the Ubuntu Server
1. Install Required Packages
sudo apt updatesudo apt install rsync openssh-server -ysudo systemctl enable sshsudo systemctl start ssh2. Create Dedicated Backup User
Never use root for backups. Create a dedicated user with minimal permissions:
sudo useradd -m -s /bin/bash synology-backupsudo passwd synology-backup# Set a strong password3. Create Backup Directory
sudo mkdir -p /backup/synologysudo chown synology-backup:synology-backup /backup/synologysudo chmod 750 /backup/synology
# Verify available space (you should see ~136GB free)df -h /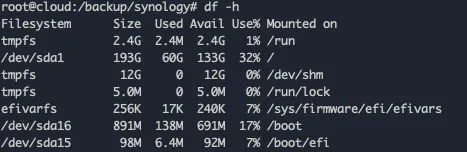
4. Fix Oracle Cloud SSH Configuration
This is the critical step. Oracle Cloud uses configuration includes that override your main sshd_config file:
# Check for override filesls -la /etc/ssh/sshd_config.d/
# You'll likely see 50-cloud-init.conf or similarsudo nano /etc/ssh/sshd_config.d/50-cloud-init.confChange these lines:
# FROM:PasswordAuthentication no
# TO:PasswordAuthentication yesAlso ensure these are set in the main config:
sudo nano /etc/ssh/sshd_configAdd or modify:
PasswordAuthentication yesPubkeyAuthentication yesKbdInteractiveAuthentication yesUsePAM yesPermitRootLogin noRestart SSH (note: it’s ssh not sshd on Ubuntu):
sudo systemctl restart ssh5. Verify Configuration
This is crucial—verify the active configuration:
sudo sshd -T | grep passwordauthentication# Should show: passwordauthentication yesIf it still shows “no”, check for other override files:
sudo grep -r "PasswordAuthentication" /etc/ssh/![]()
Test Connection from Synology
SSH into your Synology NAS and test:
# Test SSH connectionssh synology-backup@100.72.22.38# Should prompt for password
# Test rsyncrsync -avz --dry-run /volume1/homes/ synology-backup@100.72.22.38:/backup/synology/test/Tip
If you still can’t connect, check Oracle Cloud Security Lists. By default, they allow SSH from anywhere, but if you’ve modified them, ensure your Tailscale subnet (100.0.0.0/8) is allowed.
Configuring rsync Daemon (Recommended)
While SSH-based rsync works, HyperBackup’s UI works better with rsync daemon mode, which provides module discovery and better integration.
1. Create rsync Configuration
sudo nano /etc/rsyncd.confAdd this configuration:
uid = synology-backupgid = synology-backupuse chroot = nomax connections = 10pid file = /var/run/rsyncd.pidlog file = /var/log/rsyncd.logtimeout = 300
[synology_backup]path = /backup/synologycomment = Synology HyperBackup Storageread only = nolist = yesauth users = synology-backupsecrets file = /etc/rsyncd.secretshosts allow = 100.0.0.0/8Note
The hosts allow line restricts access to Tailscale IPs only (100.0.0.0/8 subnet). This ensures only devices on your Tailscale network can connect.
2. Create Credentials File
sudo nano /etc/rsyncd.secretsAdd (replace with your actual password):
synology-backup:YOUR_STRONG_PASSWORD_HERESet proper permissions:
sudo chmod 600 /etc/rsyncd.secretssudo chown root:root /etc/rsyncd.secrets3. Enable and Start rsync Daemon
sudo systemctl enable rsyncsudo systemctl start rsync
# Verify it's runningsudo systemctl status rsync
# Check it's listening on port 873sudo ss -tlnp | grep 873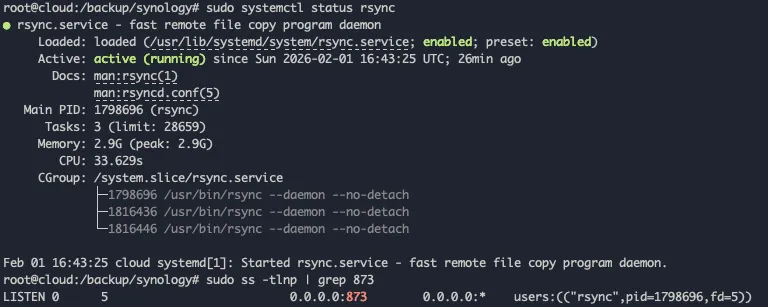
4. Test rsync Daemon from Synology
# List available modulesrsync synology-backup@100.72.22.38::
# Should show:# synology_backup Synology HyperBackup Storage
# Test with passwordexport RSYNC_PASSWORD='YOUR_PASSWORD'rsync -avz --dry-run /volume1/homes/merox/ synology-backup@100.72.22.38::synology_backup/test/Configuring HyperBackup
Now for the easy part—setting up HyperBackup to use your Oracle Cloud instance.
1. Create Backup Task
- Open HyperBackup in DSM
- Click + (Create backup task)
- Select Folders and packages
- Choose rsync as the file server
- Select Multiple versions (recommended for versioning)
- Choose rsync-compatible server
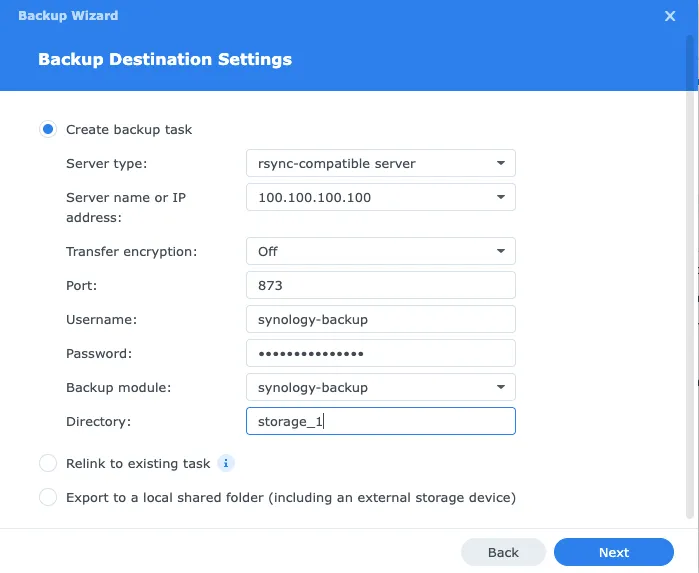
2. Connection Settings
Here’s where the rsync daemon configuration pays off:
Server Configuration:
- Server name or IP address:
100.72.22.38(your Tailscale IP) - Port:
873(not 22!) - Transfer encryption: ❌ Disabled (Tailscale already encrypts)
- Username:
synology-backup - Password: Your password from
/etc/rsyncd.secrets
Backup Location:
- Backup module: Click and select
synology_backup - Directory: Leave blank or add a subfolder like
nas-backup
Warning
Critical: When using rsync daemon (port 873), you MUST disable “Transfer encryption”. The option tries to use SSH which isn’t available on port 873. Don’t worry—Tailscale provides encryption at the network level.
3. Select Backup Data
Choose the folders you want to backup. For a typical setup:
/homes- User home directories/photo- Photo library/documents- Important documents/docker- Docker configurations (if using Docker)
4. Backup Settings
Recommended settings:
- Task name:
Oracle Cloud Backup - Compress backup data: ✅ Enabled (saves bandwidth and storage)
- Enable backup schedule: ✅ Enabled
- Schedule: Daily at 2-3 AM (off-peak hours)
- Enable integrity check schedule: ✅ Enabled
- Schedule: Weekly on Saturday evenings
- Enable client-side encryption: ✅ Highly Recommended
Tip
Client-side encryption is crucial! Even though Tailscale encrypts the transfer, client-side encryption protects your data at rest. If someone gains access to your Oracle Cloud instance, they can’t read your backups without your encryption password.
5. Rotation Settings
Smart Recycle with version limits:
- Maximum number of versions: 3-5 (adjust based on your 200GB limit)
- Smart Recycle: Enabled (automatically removes oldest versions when space is low)
With 136GB available and smart rotation, you can comfortably backup 50-100GB of data with multiple versions.
Monitoring and Maintenance
Check Backup Status
On Ubuntu, monitor your backups:
# View backup sizedu -sh /backup/synology/*
# Monitor in real-time during backupwatch -n 10 du -sh /backup/synology
# Check what's being backed upls -lah /backup/synology/Monitor with Netdata
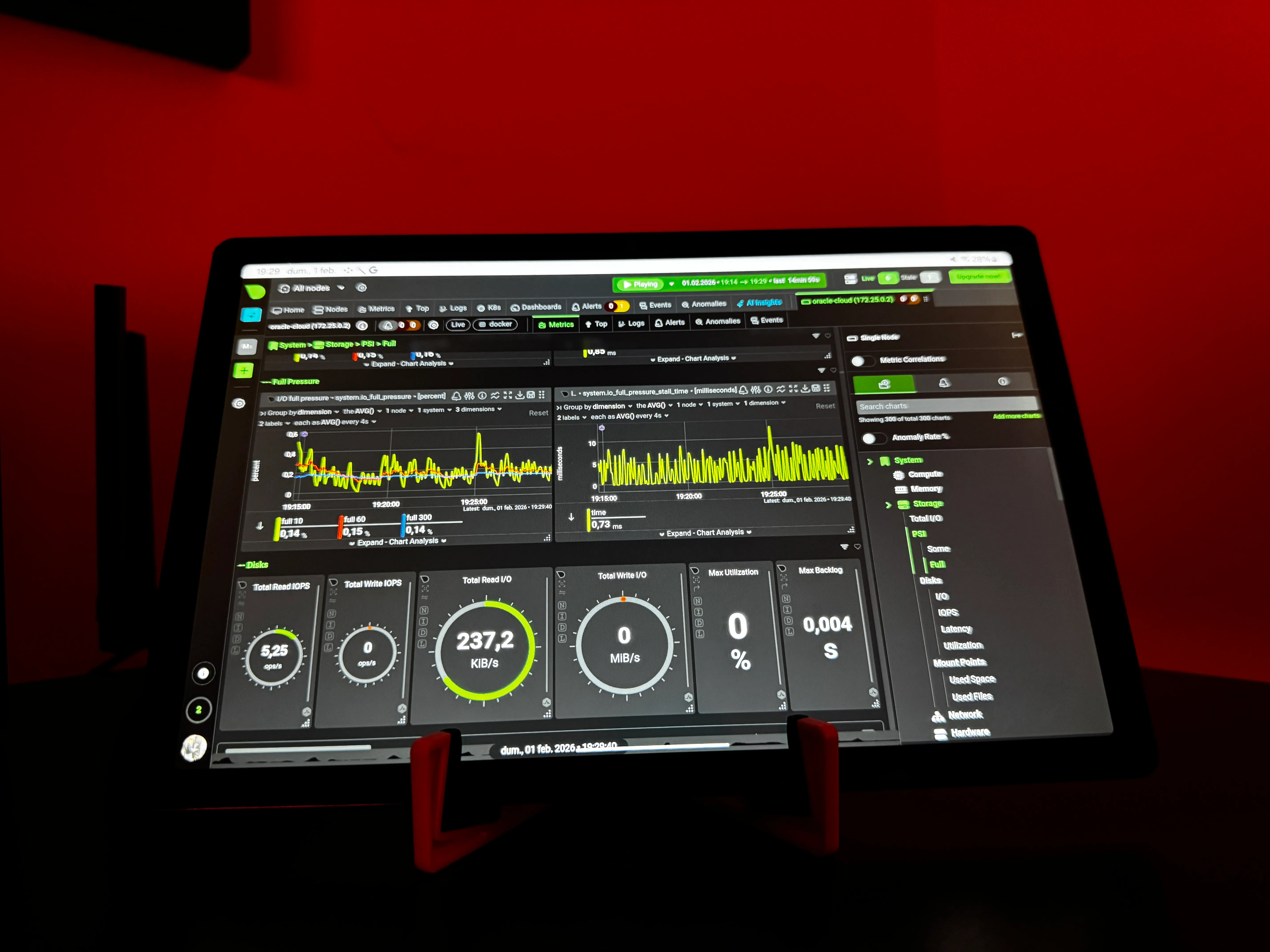
If you noticed in my Oracle Cloud instance, I have Netdata running. It’s perfect for monitoring:
# Access at: http://100.72.22.38:19999Netdata shows:
- Disk I/O during backups
- Network traffic over Tailscale
- Storage usage trends
- System load
View Logs
# rsync daemon logssudo tail -f /var/log/rsyncd.log
# SSH authentication logssudo tail -f /var/log/auth.log | grep synology-backupTroubleshooting Common Issues
”Failed to connect to backup destination”
Cause: Transfer encryption enabled with rsync daemon
Fix: Disable “Transfer encryption” in HyperBackup when using port 873
”Permission denied (publickey)”
Cause: Oracle Cloud’s SSH config overrides
Fix: Check /etc/ssh/sshd_config.d/ for override files and verify with sudo sshd -T | grep passwordauthentication
Backup Slower Than Expected
Causes:
- First backup transfers everything (takes hours)
- Tailscale relay instead of direct connection
- Synology CPU limited
Monitoring:
# On Oracle Cloud, check network speedsudo iftop -i tailscale0
# On Synology, check HyperBackup logscat /var/log/synopkg.log | grep HyperBackupSolutions:
- Ensure Tailscale uses direct connection (check
tailscale status) - Schedule backups during low-usage periods
- Enable compression in HyperBackup (reduces data transfer)
Running Out of Space
Check usage:
# See what's using spacedu -h /backup/synology/ | sort -rh | head -20
# Check available spacedf -h /Solutions:
- Reduce version retention in HyperBackup rotation settings
- Exclude large unnecessary folders (media caches, temp files)
- Delete old backups manually if needed
Security Best Practices
1. Use SSH Keys (Optional but Recommended)
After confirming password authentication works, migrate to SSH keys:
On Synology:
ssh-keygen -t ed25519 -C "synology-hyperbackup"cat ~/.ssh/id_ed25519.pubOn Ubuntu:
sudo su - synology-backupmkdir -p ~/.sshnano ~/.ssh/authorized_keys# Paste Synology's public keychmod 600 ~/.ssh/authorized_keysexitThen disable password authentication:
sudo nano /etc/ssh/sshd_config.d/50-cloud-init.conf# Change back to: PasswordAuthentication nosudo systemctl restart ssh2. Firewall Configuration
Since everything is over Tailscale, you don’t need to open ports publicly:
# If you have ufw enabled, allow SSH only from Tailscalesudo ufw allow from 100.0.0.0/8 to any port 22sudo ufw allow from 100.0.0.0/8 to any port 8733. Regular Updates
Keep your Oracle Cloud instance updated:
# Weekly updatessudo apt update && sudo apt upgrade -y
# Enable unattended security updatessudo apt install unattended-upgrades -ysudo dpkg-reconfigure -plow unattended-upgrades4. Backup the Encryption Key
CRITICAL: If you enabled client-side encryption in HyperBackup, save your encryption password in a password manager. Without it, your backups are permanently unrecoverable.
Why This Setup Works in 2026
This configuration aligns with several key trends in homelab and backup strategies:
Oracle Cloud’s Generous Free Tier
Oracle’s commitment to their Always Free tier remains strong into 2026. Unlike other providers who’ve quietly reduced free offerings, Oracle continues providing:
- 4 OCPUs Ampere A1 compute
- 24GB RAM
- 200GB block storage
- Unlimited ingress traffic
- 10TB monthly egress
This makes it one of the best platforms for cost-free off-site backups.
Tailscale’s Growing Adoption
Tailscale has become the de facto standard for homelab networking in 2026. Its zero-config approach and WireGuard-based performance have made traditional VPN setups obsolete for personal use. The free tier’s 100-device limit is more than enough for most homelabs.
The 3-2-1-1-0 Backup Strategy
Modern backup best practices have evolved to 3-2-1-1-0:
- 3 copies of data
- 2 different media types
- 1 copy off-site (Oracle Cloud satisfies this)
- 1 copy offline/immutable (HyperBackup’s versioning provides this)
- 0 errors in backups (HyperBackup’s integrity checks ensure this)
This Oracle Cloud setup perfectly satisfies the off-site requirement without recurring costs.
rsync’s Reliability
Despite newer backup tools emerging, rsync remains the gold standard for incremental backups. Its efficiency, reliability, and ubiquity make it ideal for NAS backups. Synology’s HyperBackup builds on rsync while adding versioning, encryption, and scheduling.
Cost Analysis
Let’s compare this setup to commercial alternatives:
Commercial Cloud Backup (200GB):
- Synology C2: $60/year
- Backblaze B2: 28.80/year (+ egress fees)
- AWS S3: 55.20/year (+ egress fees)
This Setup:
- Oracle Cloud Always Free: $0
- Tailscale Free Tier: $0
- Total: $0/year
Savings: $60-300/year depending on chosen service and data transfer
Tip
For a typical homelab with 50-100GB of important data, this setup saves $60-120 annually compared to commercial backup services, while providing the same (or better) security and control.
Limitations to Consider
This setup isn’t perfect for everyone:
Storage Limits
200GB total block storage with 5 volume backups means you’re limited to ~180GB for actual backup data (reserving some for OS and overhead). If you need more:
- Use multiple Oracle Cloud accounts (one per person in your household)
- Supplement with local backups
- Consider paid cloud storage for large media libraries
Backup Speed
Incremental backups are fast, but initial uploads can take 8-24 hours for 100GB over residential internet. Plan accordingly:
- Start first backup on a weekend
- Use compression to reduce data transfer
- Schedule during off-peak hours
No Official SLA
Oracle’s Always Free tier has no SLA. While outages are rare, your backup destination could theoretically be unavailable when needed. Mitigate this with local backup copies.
Conclusion
Setting up Synology HyperBackup with Oracle Cloud’s Always Free tier provides a professional-grade, zero-cost off-site backup solution. The key challenges—Oracle Cloud’s SSH configuration and HyperBackup’s rsync daemon integration—are easily overcome with the right configuration.
After the initial setup, your backups run automatically, protected by both Tailscale’s network encryption and HyperBackup’s client-side encryption. Combined with local backup copies, you have a robust 3-2-1 backup strategy without monthly fees.
The combination of Oracle Cloud, Tailscale, and Synology HyperBackup creates a backup solution that would cost $60-120/year with commercial providers, completely free. For homelab enthusiasts in 2026, it’s one of the best setups available.